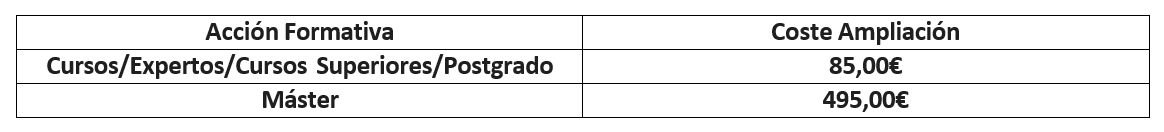
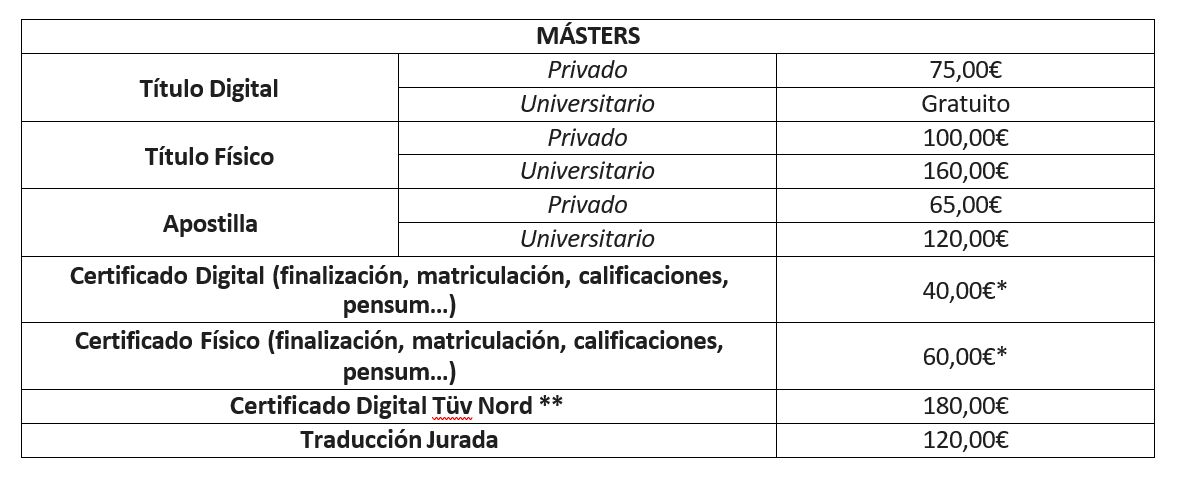
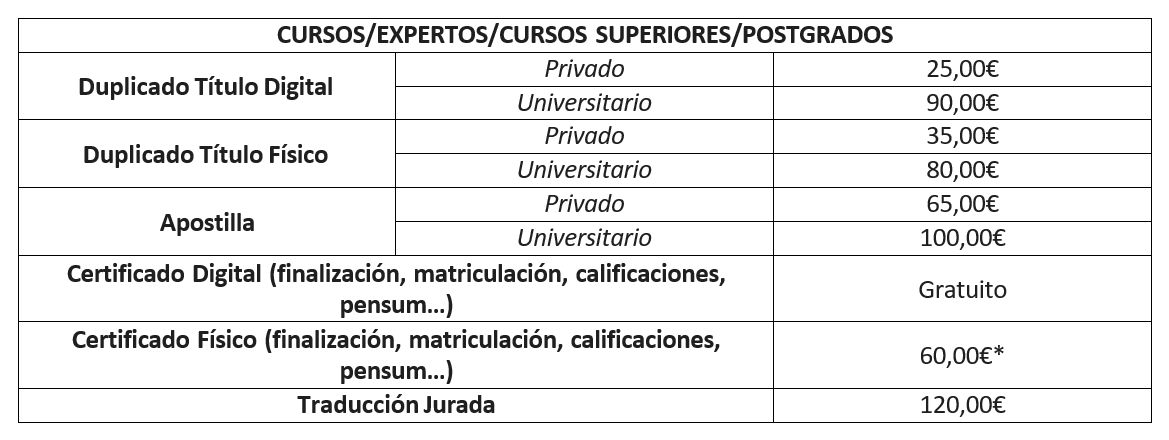
- Introduction
- State of the art
- Analysis
- Actions
- Unit summary
- Introduction
- Detection
- Analysis
- General protections
- Unit summary
- Introduction
- Good practices
- Risk management and mitigating factors
- Threats and vulnerabilities
- Unit summary
- Introduction
- Definition and objectives
- Regulations
- Cybersecurity Management Systems
- Unit summary
- Introduction
- Security plan
- Safe development
- Cases
- Unit summary
- Introduction
- Identity management
- Authentication
- Authentication schemes
- Unit summary
- Introduction
- Threat models
- Assessment
- Risks
- Unit summary
- Introduction
- Management
- Active storage
- Passive storage
- Unit summary
- Introduction
- Types of social media
- Social media concepts
- Social media security
- Unit summary
- Introduction
- Social media threats
- Mitigating mechanisms
- Security tools
- Unit summary
- Introduction
- DOXING techniques
- SOCINT techniques
- Tools
- Unit summary
- Introduction
- Infoxication
- Information analysis
- Fake news detection techniques
- Unit summary